Week 1:
Ethical hackers: people that have hacking skills employed by a company to perform penetration tests
Penetration test (pentest): legally attempt to break in a company’s network through it’s weakness, testers only to report their findings
Security test: includes pentest + analyzing company’s security policy and procedures, testers offer solutions to secure/protect the network.
What makes them different from other hackers:
- Ethical hackers obtain permission from network owners to hack data
- Ethical hackers are generally white hats(hackers who obey the law)
Penetration-Testing methodologies:
White box model: Tester knows everything about the network topology and technology, company staff knows about the attempt pentest
Black box model: Tester did not have any information about the network, company staff did not know about the attempt pentest, also challenges the security personnel are able to detect an attack
Grey box model: Mix of both models, company gives tester partial info
Penetration-Testing process:
- Defining the scope of the test: where, what, who, how long (will be tested)
- Perform the pentest
- Reporting the pentest
Penetration-Testing common techniques:
- Passive Research
- Open Source Monitoring
- Network mapping and OS
fingerprinting - Spoofing
- Network Sniffing
- Trojan attacks
- Brute-force
- Vulnerability scanning
- Scenario analysis
In Pentest, there are 2 teams: red team and blue team
Red team: to attack the server
Blue team: to defend against red team, anticipating their attacks
To be Ethical Hacker, we need certifications such as OSSTMM
Every country has their own laws about hacking, so it’s better to read the country’s law about technology systems. One mistake can makes an ethical hacker to simply hacker.
Week 2:
Intelligence gathering: basically information gathering for preparation of ethical hacking such as company name, address, website, pentest objecttives, types, servers, etc.
There are many tools to achieve this such as paros proxy.
Also by using whois command, one can find domain info and IP address of the target company.
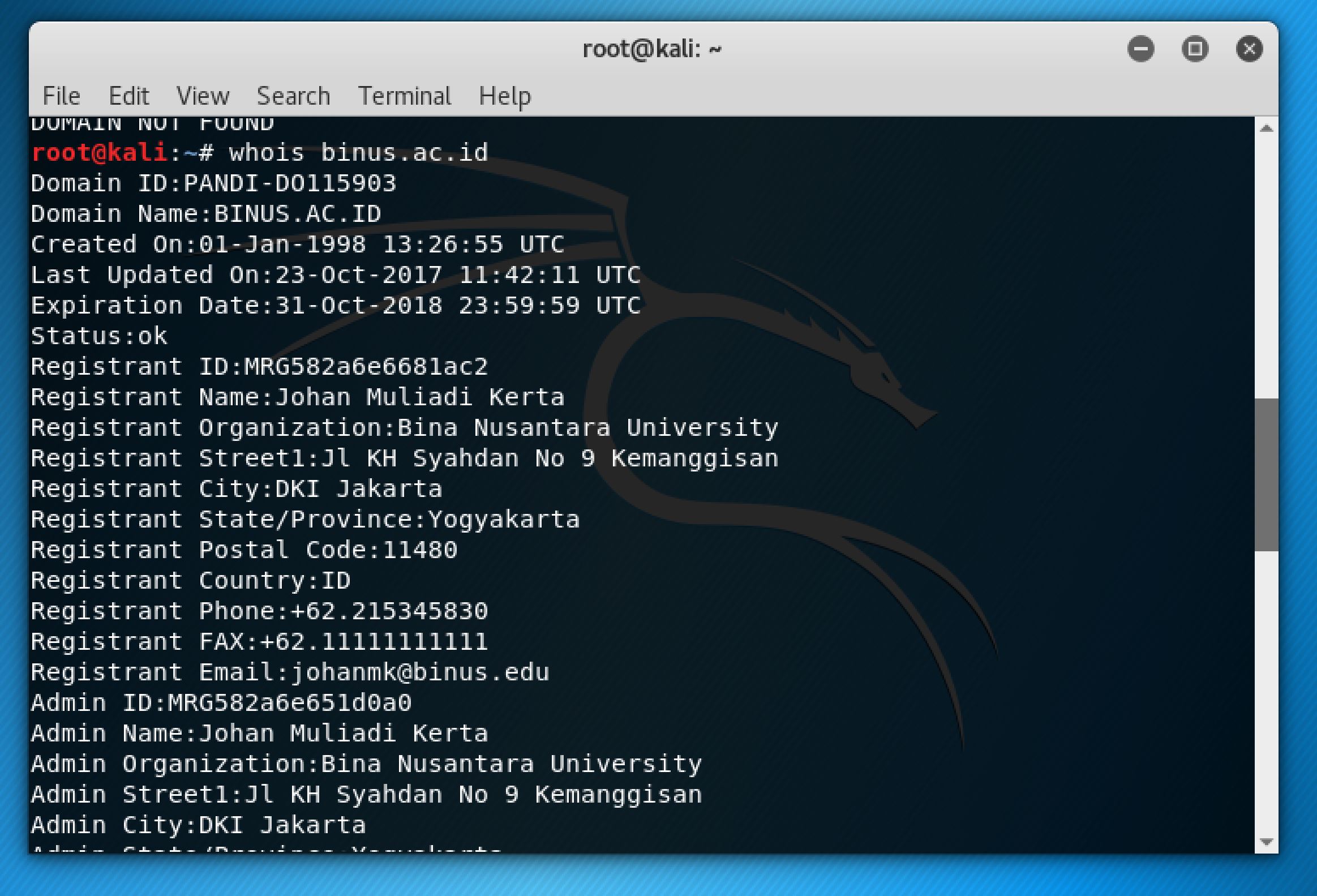
Also by HTTP methods can find server info, but cannot if it’s guarded by firewall
Other methods is by cookies or web bugs
