DNS:
what dns do?
resolve host names to ip address
simple but extremely vunerable because using simple protocol (using UDP)
DNS is mapping machine
DNS zone transfer:
– enables you to see all hosts on a network
– GIves you organization’s network diagram
Zone transfer using enum:
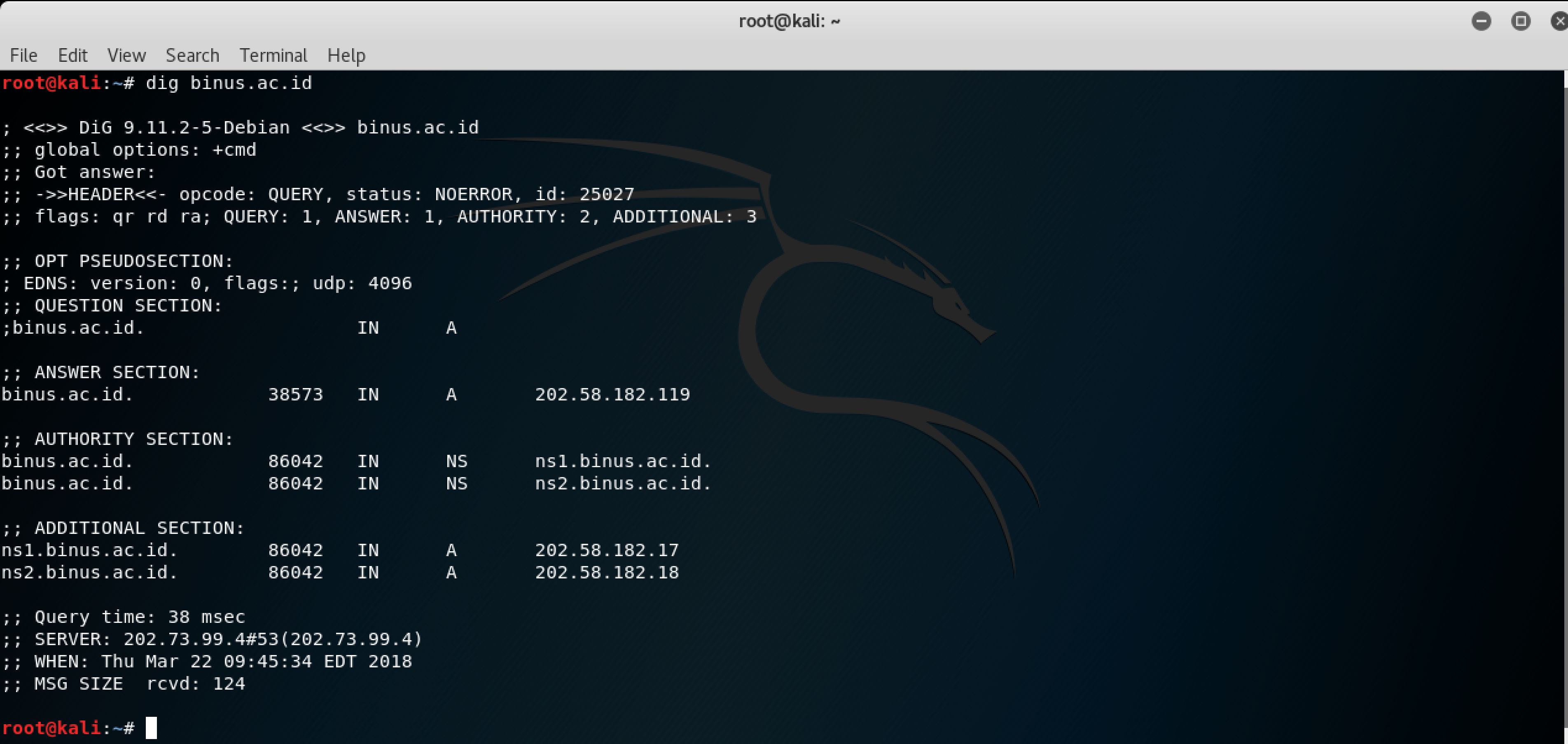
use DIG SOA (websitename)
dig command: enumerating records used by a website
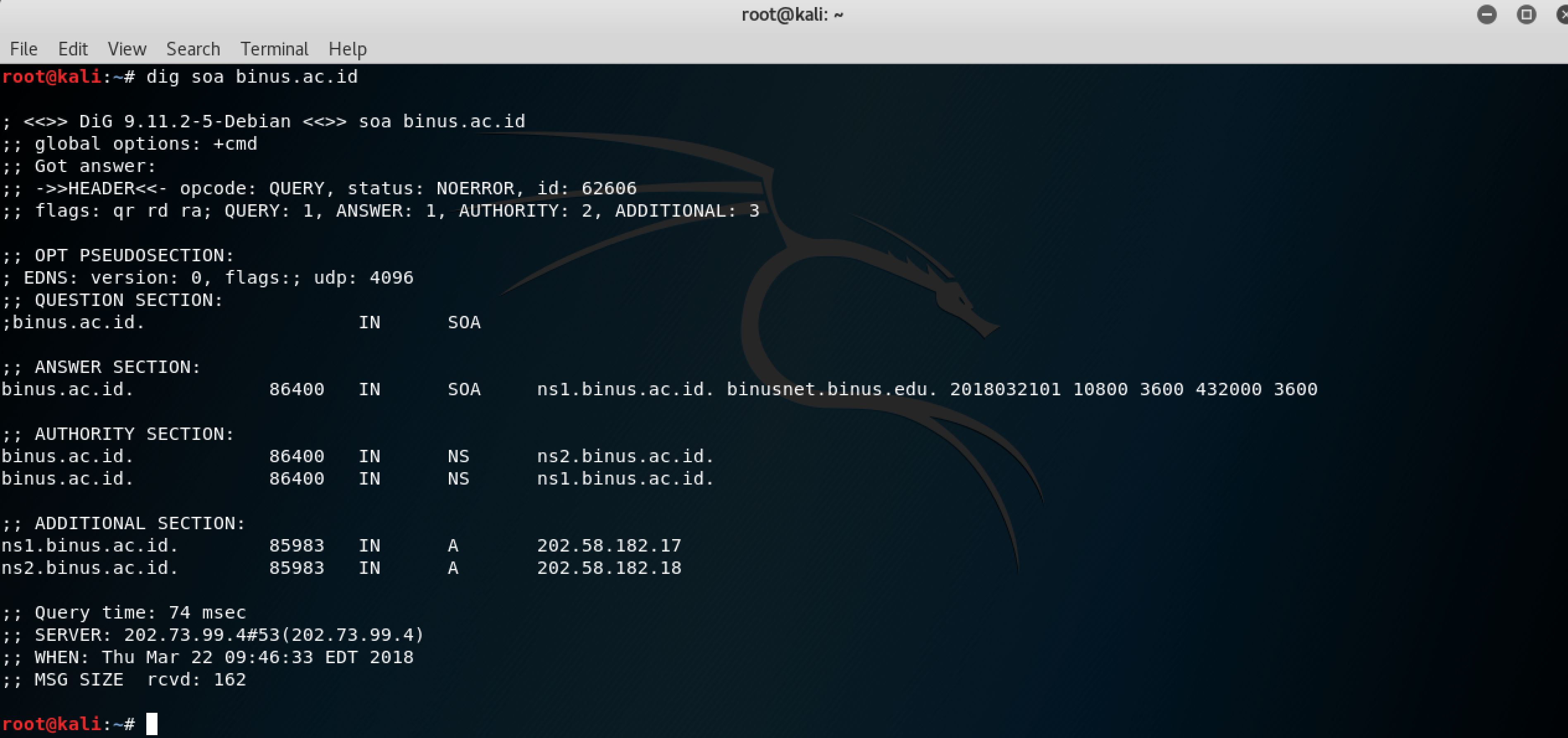
dig soa command: enumerating SoA (Start of Authority)records
————————————————————————————
utilizing search engine
GOOGLE also can list info leak out in your system
one of the tools: Maltego
?It can find the relationships, which (people) are linked to, including their social profile, mutual friends, companies that are related to the information gathered, and websites.
?Also we can gather information related to any infrastructure, we can gather relationship between domains, DNS names, and net blocks.
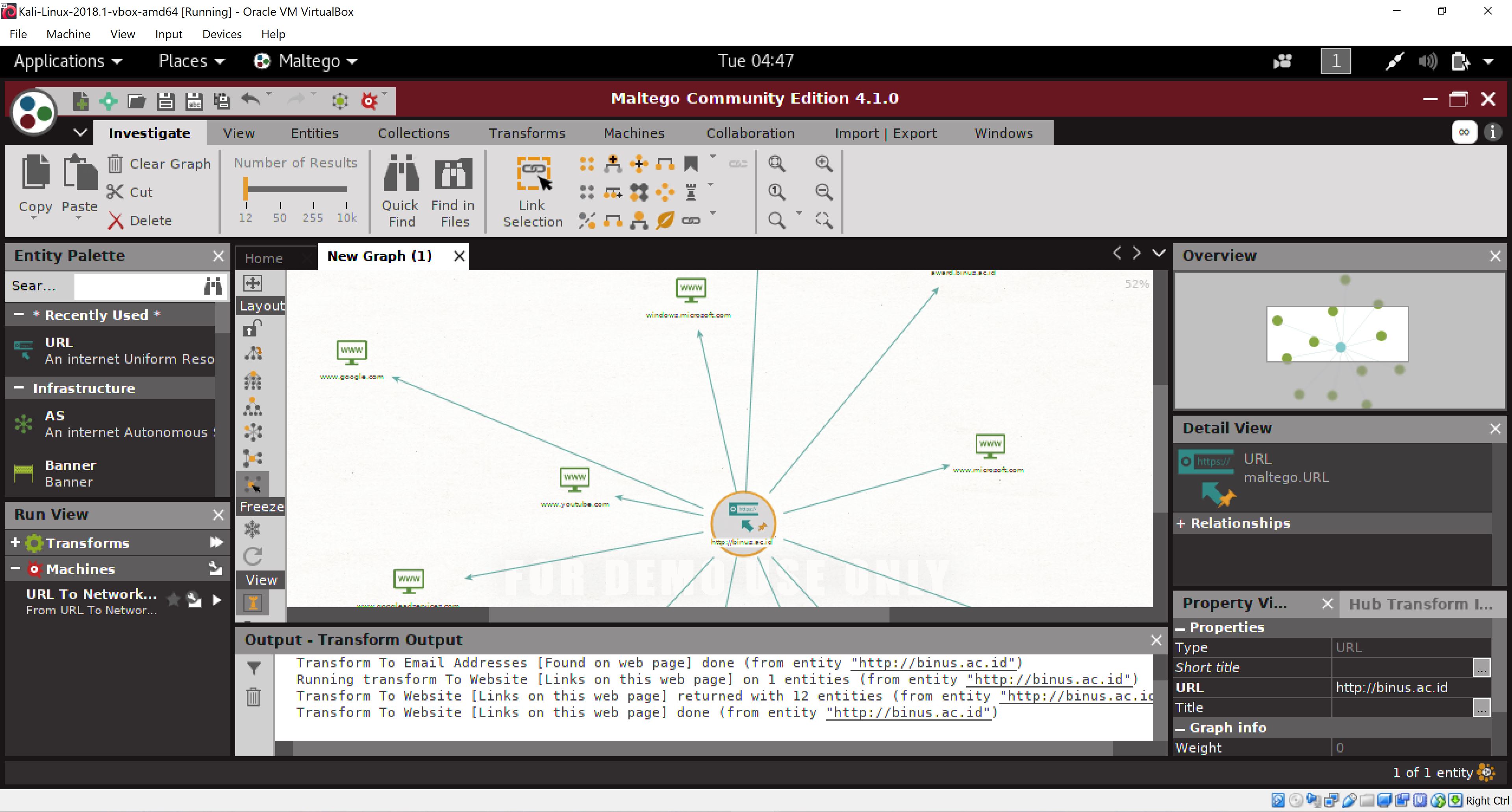
I used binus.ac.id as test subject and it shows multiple websites linked to the website.
Google hacks: Google Dorks
can find sensitive files
used for finding backup mistakes by admins
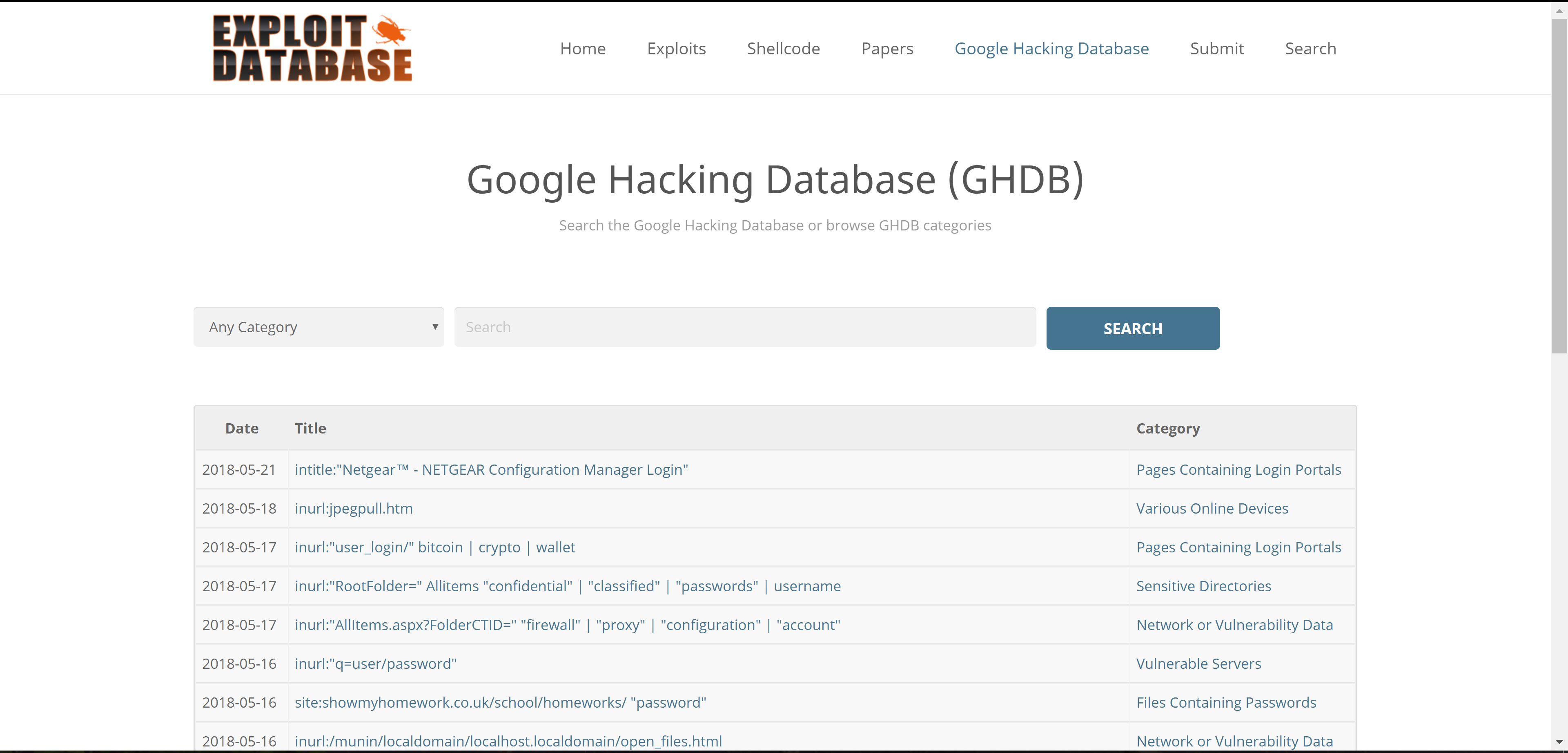
For example, I’ll just search for file containing passwords, 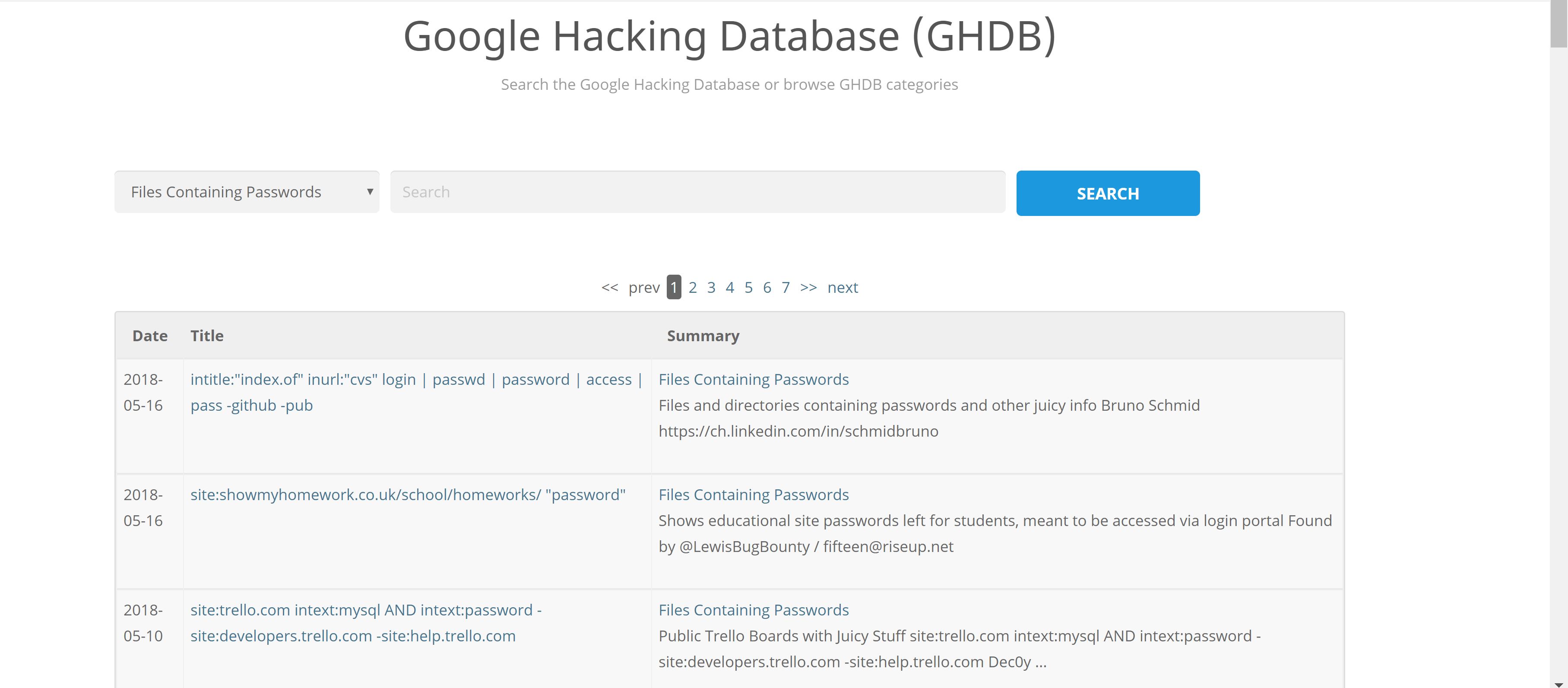
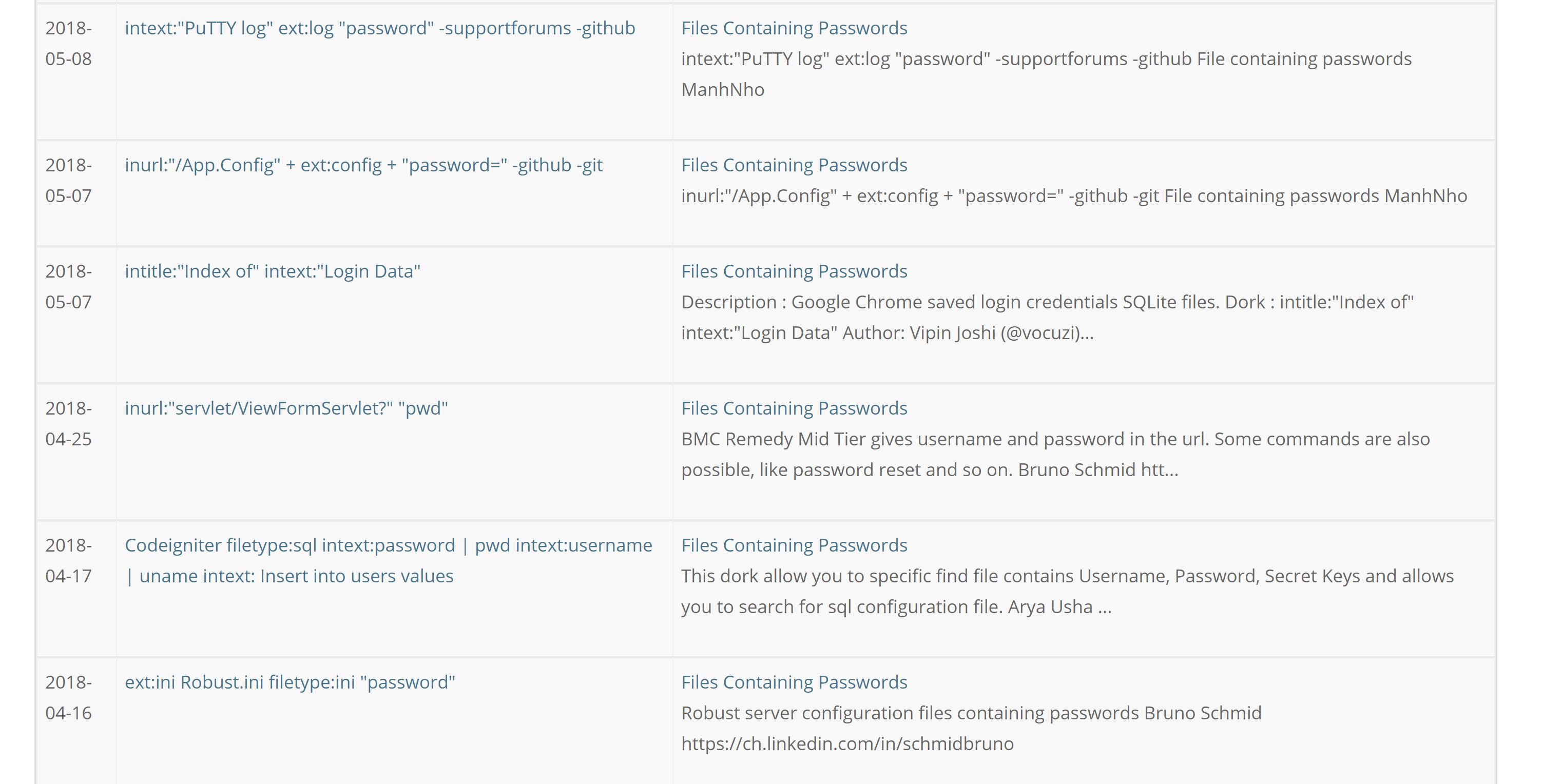
single point error: 1 DNS only, subjected to be attacked
Email use TCP protocol
front end: Email service
back end:
HTTP(port 80) connected to
SMTP(port 25) (Exclusive)
and
POP(port 110)
small note: well known ports(0 – 1023)
(used command: host (website), dig (website))
